With global cybercrime estimated to cost the world $10.5 trillion annually by 2025, it is important to know about the potential threat cybercrime poses, the impact it has and what can be done about it. One of the biggest problems is that there is just so much information. Not only is the nature of threats constantly evolving, but the responses to them differ across the globe. For example, one of the newest threats to consumers is not the loss of their data, but the use of their devices for bit coin mining. In fact, Symantec, a leading American software company, found that there was an 8,500 percent increase in the detection of coin miners.
Impact on business:
Damage to Reputation/Brand- It is important to remember that information put on the web stays there forever and it is possible that any online accounts could be hacked and personal information could be put on display for the entire world to see. It is important to think about this when considering the proper way to protect your customer and company data from cybercriminals. From a global survey, the lasting impact of a data breach on customers is so significant that 95% of participants would be willing to seek legal action against a company that didn’t properly protect their information. The survey also revealed that customers are prepared to break all ties with
any company that is a victim of data breach. A data breach is detrimental to your company because it not only destroys customer trust, but it also causes the public to perceive your company as ill-equipped and easily hacked.
Intellectual Property Damage- A cybercriminal stealing ideas and plans could easily expose them to your competitors, making these ideas useless, costing your business months or even years of valuable work.
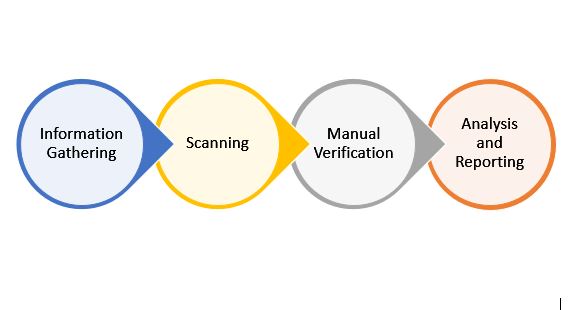
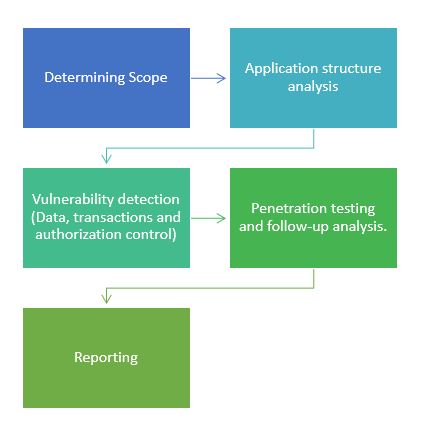
VULNERABILITY ASSESSMENT AND PENETRATION TESTING
Vulnerability Assessment and Penetration Testing involves extracting loop holes in the company's network system.
We at NSS help curb these vulnerabilities in your company's digital network through Manual Verification and Testing.
We advise on effective solutions to secure your network by a thorough analysis of:
- Identifying vulnerabilities.
- Conducting a non-invasive test of the network’s external security strength.
- Independent analysis of network/vulnerability identification.
WEB APPLICATION TESTING
In an increasingly networked world, a lot of information has been displayed and interconnected via web platforms. This creates an increased risk to information and the analysis of Web Application is necessary to create a baseline so that one understands the present state better and can thus appreciate the findings and recommendations. We provide a rigorous testing platform to test components to expose their vulnerabilities and offer solutions to improve the security of your application.
GSM ENCRYPTION
Over the 15 years that NSS has been involved with mobile application security, both the device as well as the security ecosystem have transformed to an unrecognisable level. The mobile phone is ubiquitous in business and in personal use. Smartphone apps have inundated the technology landscape. The mobile is the new electronic leash. It is carried everywhere, is the frontline trenches with electronic access to well protected intelligence. It can gets exposed, lost, stolen and hacked. We all pay the price for preferring convenience over security, but we don’t always realise that there are ways to minimise potential leaks and thereby, damage.
NSS has extensive experience in mobile security software, from data and device security, to the last bastion of protection – encryption. With two patents in encryption technology, NSS assists key corporate and institutional clients with their secure mobile communications requirements.

COMPUTER EMERGENCY RESPONSE
A computer emergency response team (CERT) is an expert group that handles computer security incidents. CERTs focus on countering security breaches and denial-of-service incidents, providing alerts and incident-handling and preclusion guidelines. CERTs also conduct an ongoing public awareness campaign and engage in research aimed at improving security systems.